| Improve Netowrk performance by Tuning TCP | HAReplicator User Manual |
| Here are step-by-step instructions for tuning TCP for
Windows
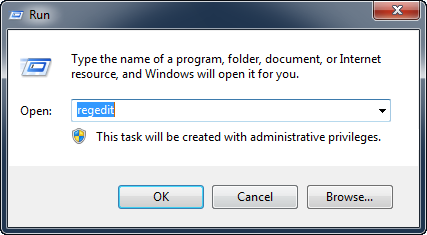
Open RegEdit by clicking on "Start -> Run", typing in RegEdit and clicking "OK".
Press the OK button to open RegEdit program.
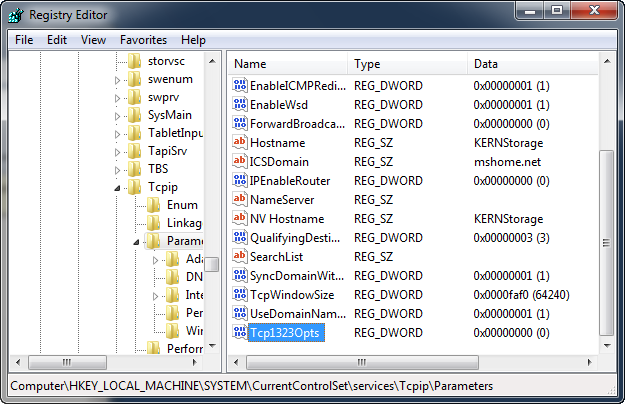
Browse to the TCP/IP registry keys under
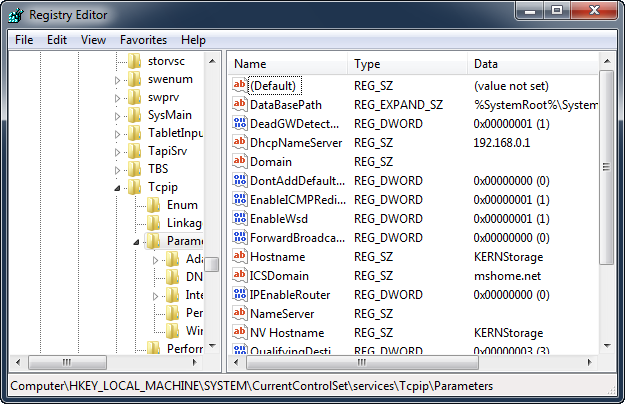
Adjust the registry keys to tweak your network performance. To tune TCP/IP you will need to add specific DWORD values, unless your system has been tuned previously. To add a value, right click in the right window showing the key values and select "New -> DWORD value".
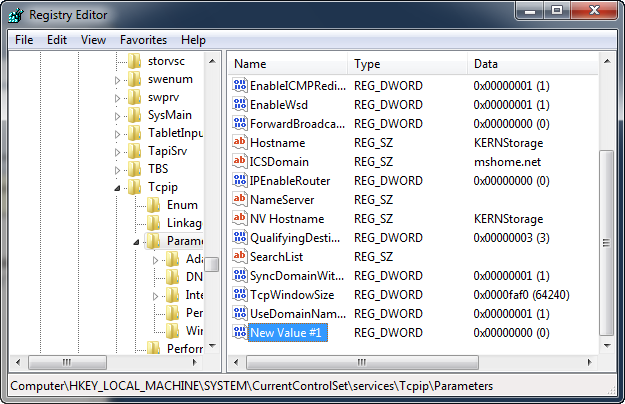
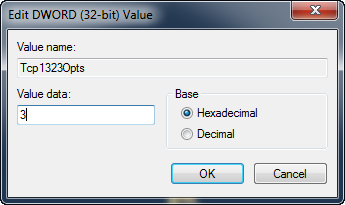
Rename this "New Value" to the option you wish to set. The first and most important is to enable RFC 1323 features by editing the new option to "Tcp1323Opts" and hitting Enter.
Double-click your new value to open a dialog box and enter a valid value range and select "OK". For "Tcp1323Opts" you want to enter "3", which turns on all features (see the list below if you are interested in the details).
You should now see your new REG_DWORD value (In this case option "TCP1323" is REG_DWORD with value 3. Repeat the above steps to add DWORD registry parameters "GlobalMaxTcpWindowSize"
and "TcpWindowSize", Detailed descriptions of the registry parameters Value Type: REG_DWORD—number (flags) Valid Range: 0, 1, 2, 3 0 (disable RFC 1323 options) 1 (window scaling enabled only) 2 (timestamps enabled only) 3 (both options enabled) Default: No value. The default behavior is as follows: do not use the
Timestamp and Window Scale options when initiating TCP connections but use
them if the TCP peer that is initiating communication includes them in the
SYN segment. GlobalMaxTcpWindowSize Value Type: REG_DWORD—Number of bytes Valid Range: 0–0x3FFFFFFF (1073741823 decimal; however, values greater than 64 KB can only be achieved when connecting to other systems that support RFC 1323 window scaling, which is discussed in the TCP section of this article.) Default: This parameter does not exist by default. Description: The GobalMaxTcpWindowSize parameter can be used to set the receive window on a per-interface basis. This parameter can be used to set a global limit for the TCP window size on a system-wide basis. TcpWindowSize Value Type: REG_DWORD—number of bytes ValidRange: 0–0x3FFFFFFF (1073741823 decimal). In practice the TCP/IP stack will round the number set to the nearest multiple of maximum segment size (MSS). Values greater than 64 KB can be achieved only when connecting to other systems that support RFC 1323 Window Scaling, which is discussed in the "Transmission Control Protocol (TCP)" section of this article. Default: The smaller of the following values: 0xFFFF EnablePMTUDiscovery Value Type: REG_DWORD—Boolean Valid Range: 0, 1 (false, true) Default: 1 (true) Description: When this parameter is set to 1 (true) TCP attempts to discover the Maximum Transmission Unit (MTU), or largest packet size, over the path to a remote host. By discovering the Path MTU (PMTU) and limiting TCP segments to this size, TCP can eliminate fragmentation at routers along the path that connect networks with different MTUs. Fragmentation adversely affects TCP throughput and network congestion. Setting this parameter to 0 (not recommended) causes an MTU of 576 bytes to be used for all connections that are not to destinations on a locally attached subnet. MTU Value Type: REG_DWORD—number Valid Range: 88–the MTU of the underlying network Default: 0xFFFFFFFF Description: This parameter overrides the default Maximum Transmission Unit (MTU) for a network interface. The MTU is the maximum IP packet size, in bytes, that can be transmitted over the underlying network. For values larger than the default for the underlying network, the network default MTU is used. For values smaller than 88, the MTU of 88 is used. |
|
SUPPORT
- Forum
- Support Ticket
- [email protected]

- Voice Mail:
- +1 (518) 289-4888